Intelligently mitigate risk, streamline compliance and stay secure
Build resilient cyber risk and compliance programs powered by AI.
Trusted by hundreds of CISOs, information security leaders and risk managers worldwide






.png?width=130&height=60&name=image%2048%20(2).png)

Go beyond tick-box risk and compliance for cyber with AI-powered solutions that engage the entire business
Anthony Stevens, CEO of 6clicks, discusses the company's mission and market differentiation.

Security compliance
Centralize and streamline multi-framework compliance from inception to audit.
-1.png)
IT risk management
Intelligently manage your risk profile to make better decisions while keeping your company safe.
Vendor management
Confidently engage vendors in line with their criticality and rapidly identify and treat vendor non-compliance.

Incident management
Capture, respond and learn from incidents and breaches while ensuring minimal disruption to business operations.
Go beyond tick-box risk and compliance with
AI-powered solutions that engage the entire business
Anthony Stevens, CEO of 6clicks, discusses the company's mission and market differentiation.
Connect siloed teams, data, and systems on one platform to gain central oversight, enforce best practices, prove compliance, and build trust.
.webp)
Connect siloed teams, data, and systems on one platform for central oversight, enforce best practices, prove compliance, and build trust.

Turn-key content
Access hundreds of integrated content items to expedite and simplify multi-framework compliance and effective risk management.

Analytics & dashboards
Get the full picture of your risk and compliance profile and make more informed operational and strategic decisions.

Build trust
Safely share your compliance and security posture with key stakeholders, including customers, auditors and regulators.

Continuous monitoring
Implement automated control monitoring of your cloud environments and tools for real-time compliance.
Discover how Hub & Spoke balances control and autonomy for your risk and compliance programs across distributed teams
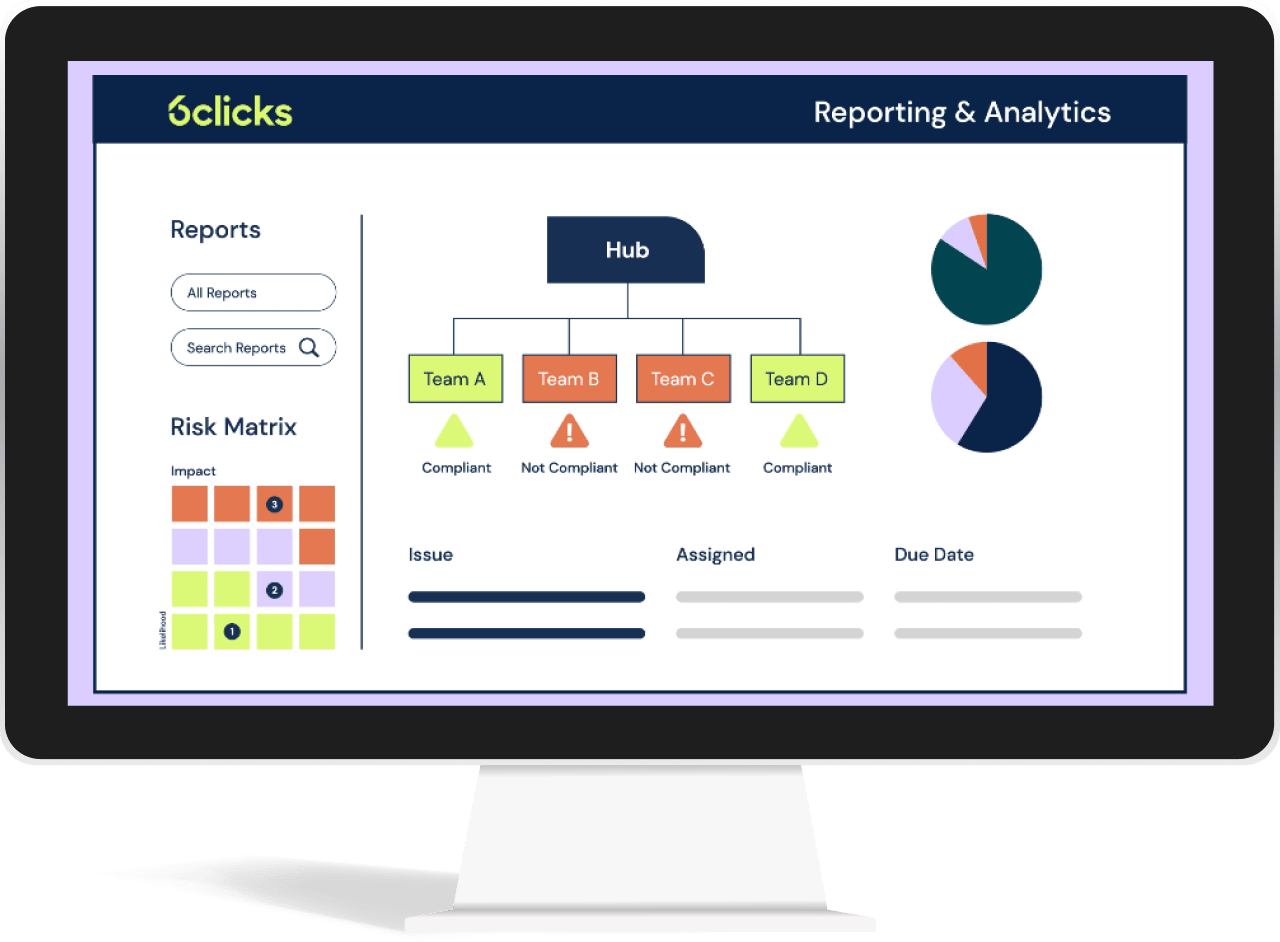
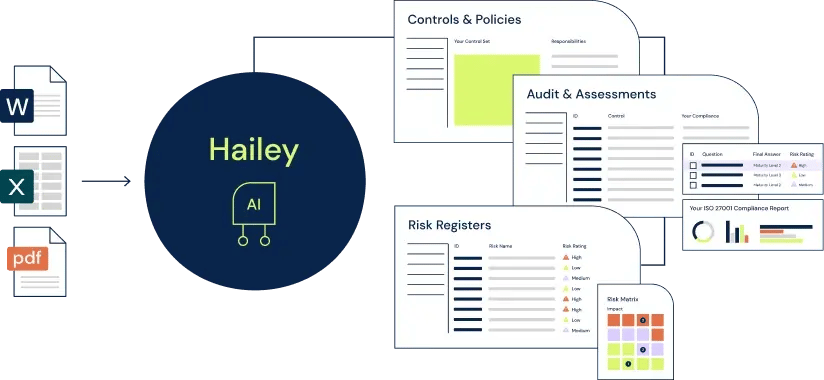
AI-powered cyber GRC
Meet Hailey, the only AI engine built for cyber GRC. Streamline and automate repetitive and highly manual processes, like compliance mapping, audit and assessment response, and control creation, and intelligently get more done with less.
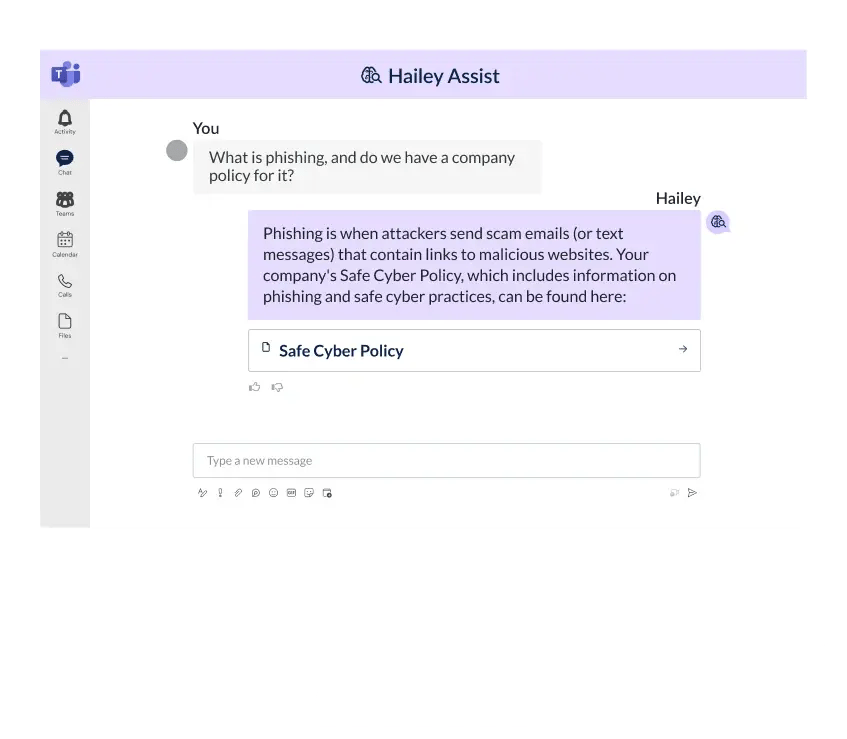
Meet your intelligent cyber GRC assistant
Experience the first-ever conversational AI assistant built for cyber GRC, Hailey Assist (beta). Its chat-style interface empowers GRC professionals to query and navigate their programs. For non-GRC professionals, it will integrate with common collaboration tools like Microsoft Teams to enhance GRC program engagement for a mature risk and security culture.
See what our customers say
One of the best solutions I have seen in a long time. 6clicks solved a major business problem we had in one centralised platform.
Trichelle Jordan, IT Operations Manager | Pitcher Partners
Other vendors we looked at drove significant implementation costs. 6clicks made it easy for us to address all of these use cases without incurring additional cost.
Paul Conway, IT Security Manager | Freightways
Going back about two years ago, we looked at different products and landed on 6clicks because it provided the scalability and ease of use we needed to encourage adoption.
Joe Kelly, VP of IT and Data Security | Lumine Group
And this is where we see the benefit of moving away from a manual GRC process into a GRC tool like 6clicks, which enables you to map each of the different standards to your control set so you only have to do the assessment once.
Belinda Edwards, Manager - Governance, Risk and Compliance | CyberCX
GRC 20/20 finds that the 6clicks solution enables organizations to be efficient, effective, and agile in their GRC related strategy and processes within an organization and across organizations and distributed/autonomous operations.
Michael Rasmussen | GRC 20/20 Research LLC
The Hub & Spoke model works for our organization by allowing us to centrally create risk assessments, questionnaires, and models while enabling our business units to complete them independently
Joe Kelly, VP of IT and Data Security | Lumine Group
Together, Veretim and 6clicks aim to optimise the risk management landscape with a fresh perspective. We are eager to embark on this journey with 6clicks.
Peter Ridgley, CEO | Verterim
We are thrilled with this partnership and the inclusion of 6clicks to our already extensive technology ecosystem. 6clicks is unique in offering a platform to reduce audit fatigue for security managers, bringing multiple dashboards into one view with thousands of API integrations. We are not only excited about the platform but also their culture and leadership’s commitment to the Channel!
Kelly Forsyth, CRO | IQ Wired
6clicks provides a unique GRC platform that allows for a Hub & Spoke GRC model for diversified, distributed, and autonomous businesses to manage GRC in their particular context while providing consistency in overall governance, framework, reporting, and benchmarking across business areas.
Michael Rasmussen | GRC 20/20 Research LLC
6clicks has demonstrated how the combination of AI, Hub & Spoke management and Content Library can revolutionize the practice of GRC and make it feasible for organizations of all sizes.
John Meacock, previously Global Chief Strategy Officer of Deloitte and now 6clicks Chairman of the Board | Centerstone Capital
We use Hub & Spoke globally for our cyber compliance program. Love it.
Head of Compliance | Fortune 500
The Hub & Spoke model actually resonates with us quite well in the way that we operate. Establishing it that way works well for how we wanted to set it up within the group. It’s been quite useful in addressing the challenges we had with inconsistent reporting across the business units.
Paul Conway, IT Security Manager | Freightways
No issues or complaints with the broader team - the service, advice, and hands-on assistance they have all provided to assist with developing CSIRO's instance has been outstanding.
Luke | CSIRO
One of the best solutions I have seen in a long time. 6clicks solved a major business problem we had in one centralised platform.
Trichelle Jordan, IT Operations Manager | Pitcher Partners
Other vendors we looked at drove significant implementation costs. 6clicks made it easy for us to address all of these use cases without incurring additional cost.
Paul Conway, IT Security Manager | Freightways
Going back about two years ago, we looked at different products and landed on 6clicks because it provided the scalability and ease of use we needed to encourage adoption.
Joe Kelly, VP of IT and Data Security | Lumine Group
And this is where we see the benefit of moving away from a manual GRC process into a GRC tool like 6clicks, which enables you to map each of the different standards to your control set so you only have to do the assessment once.
Belinda Edwards, Manager - Governance, Risk and Compliance | CyberCX
GRC 20/20 finds that the 6clicks solution enables organizations to be efficient, effective, and agile in their GRC related strategy and processes within an organization and across organizations and distributed/autonomous operations.
Michael Rasmussen | GRC 20/20 Research LLC
The Hub & Spoke model works for our organization by allowing us to centrally create risk assessments, questionnaires, and models while enabling our business units to complete them independently
Joe Kelly, VP of IT and Data Security | Lumine Group
Together, Veretim and 6clicks aim to optimise the risk management landscape with a fresh perspective. We are eager to embark on this journey with 6clicks.
Peter Ridgley, CEO | Verterim
We are thrilled with this partnership and the inclusion of 6clicks to our already extensive technology ecosystem. 6clicks is unique in offering a platform to reduce audit fatigue for security managers, bringing multiple dashboards into one view with thousands of API integrations. We are not only excited about the platform but also their culture and leadership’s commitment to the Channel!
Kelly Forsyth, CRO | IQ Wired
6clicks provides a unique GRC platform that allows for a Hub & Spoke GRC model for diversified, distributed, and autonomous businesses to manage GRC in their particular context while providing consistency in overall governance, framework, reporting, and benchmarking across business areas.
Michael Rasmussen | GRC 20/20 Research LLC
6clicks has demonstrated how the combination of AI, Hub & Spoke management and Content Library can revolutionize the practice of GRC and make it feasible for organizations of all sizes.
John Meacock, previously Global Chief Strategy Officer of Deloitte and now 6clicks Chairman of the Board | Centerstone Capital
We use Hub & Spoke globally for our cyber compliance program. Love it.
Head of Compliance | Fortune 500
The Hub & Spoke model actually resonates with us quite well in the way that we operate. Establishing it that way works well for how we wanted to set it up within the group. It’s been quite useful in addressing the challenges we had with inconsistent reporting across the business units.
Paul Conway, IT Security Manager | Freightways
No issues or complaints with the broader team - the service, advice, and hands-on assistance they have all provided to assist with developing CSIRO's instance has been outstanding.
Luke | CSIRO
One of the best solutions I have seen in a long time. 6clicks solved a major business problem we had in one centralised platform.
Trichelle Jordan, IT Operations Manager | Pitcher Partners
Discover our unique pricing
Unlimited user access and no additional
fees for content, frameworks or functionality.
.webp?width=459&height=595&name=image%20(2).webp)
Our newest thought leadership
Responsible AI Expert Guide
A practical guide on everything Responsible AI, including a turn-key assessment, control set and more.
Cyber Risk Management Expert Guide
We'll take you through using the included turn-key risk library to perform an effective cyber risk assessment.

Third-party Risk Management Expert Guide
Explore the common vendor assessment questionnaires, how to tailor vendor assessments and the importance of scoping assessments.
Intelligently accelerate your cyber risk and compliance program

Our newest thought leadership
Responsbile
AI Expert Guide
A guide on everything Responsible AI, including a turn-key assessment, control set and more.

Cyber Risk Management Expert Guide
We'll take you through using the included risk library as a starting point for performing a cyber risk assessment.

Third-party Risk Management Expert Guide
Explore several common vendor assessment questionnaires, tailored vendor assessments and the importance of scoping assessments








