Vulnerability Management
Import and manage your cybersecurity vulnerabilities, link directly to your information assets and associate risks and issues for remediation.
The Benefits
Easily manage your cybersecurity program by importing and linking vulnerabilities to information assets and associating risks and issues.
Integrate technical assurance and GRC
Automatically integrate scan data from Qualys, Nessus and any other vulnerability scanning tool.
Enhance overall IT risk management
Develop a refined risk-based understanding of technical vulnerability with automated ingestion of scan data from Qualys, Nessus and any other vulnerability scanning tool.
Prioritize vulnerability remediation
Take a risk-based approach to vulnerability management aligned with your overall risk-management framework.
6clicks consolidates and automates your vulnerability assessment and management processes.
The Features
Powerful features to support your growth
The 6clicks Vulnerability module is where vulnerabilities and GRC collide. Ingest your vulnerability scans from tools like Nessus and Qualys, import and link to assets in the 6clicks asset register, classify and prioritize vulnerabilities and link to risks and issues for remediation.
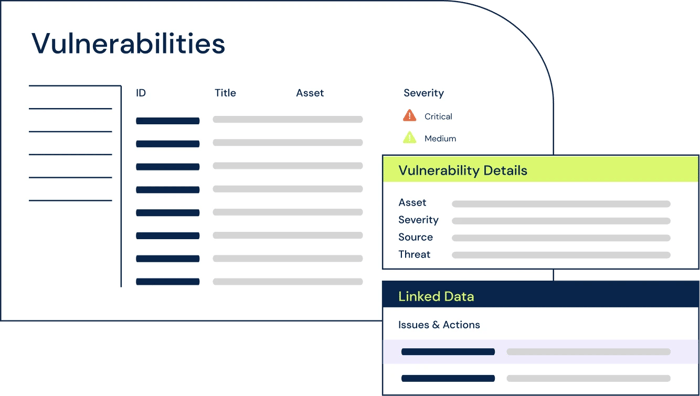
Ingest and prioritize your vulnerabilities
Import your vulnerability scans into 6clicks, then categorize, prioritize and remediate vulnerabilities.
Cross-platform linkage
Link imported assets to assets on the 6clicks asset register and link vulnerabilities to issues, incidents or risks for remediation.
Nessus & Qualys integration
Ingest scans directly from Nessus and Qualys and select the data relevant to you.
Custom mappings
Ingest vulnerability scans from any scanning tool and map data to default or custom vulnerability fields within 6clicks.
Plus, there's unlimited:
-
User licensing across all plans
-
Access to our content library
-
World-class customer support
Why businesses and advisors choose 6clicks
It's faster, easier and more cost effective than any alternative.

Powered by artificial intelligence
Experience the magic of Hailey, our artificial intelligence engine for risk and compliance.

Unique Hub & Spoke architecture
Deploy multiple teams all connected to a hub - perfect for federated, multi-team structures.

Fully integrated content library
Access 100's of standards, control sets, assessment templates, libraries and playbooks.
Featured resources
Featured resources
Intelligently accelerate your cyber risk and compliance program today
Stop wasting time with complicated pricing, longwinded consulting efforts and outdated technology.


