
Risk management has always been a cornerstone of resilient business strategy, but in today’s hyperconnected, heavily regulated environment, traditional methods are no longer enough. For CISOs, risk officers, and compliance professionals, modern risk management requires a proactive, intelligent, and integrated approach that leverages automation, AI, and real-time insights to stay ahead of threats and ensure compliance across frameworks and jurisdictions. This article outlines the essential components of a modern risk management program, along with advanced tools and strategies shaping the future of the discipline.
The shift from reactive to proactive risk management
Legacy risk management models often focused on periodic assessments and manual controls—methods that simply can’t keep up with today’s pace of change. Modern approaches are proactive, continuous, and aligned with broader business strategy.
Key shifts include:
-
Moving from point-in-time risk registers to real-time, continuously updated risk profiles
-
Treating risk as an enabler of strategy, not just a defensive function
-
Embedding risk management into daily business operations, not siloed departments
To succeed, businesses need to modernize not just their tools, but their mindset.
Core components of a modern risk management framework
Effective programs share a few foundational components:
 1. Unified risk taxonomy and governance
1. Unified risk taxonomy and governance
A consistent risk taxonomy across departments ensures alignment and clarity. Without it, risks are duplicated, misunderstood, or missed entirely. Strong governance policies guide how risks are identified, assessed, owned, and mitigated across business units, subsidiaries, and jurisdictions.
Leveraging a comprehensive risk register with customizable fields and workflows and built-in task assignment enables teams to capture critical risk information in a structured way, align activities with defined metrics and existing processes, and assign responsibilities to the appropriate stakeholders. This reinforces a consistent taxonomy and strengthens governance by embedding risk ownership and accountability.

2. Integrated risk domains
Modern risk programs must break down silos between risk types: cybersecurity, operational, compliance, strategic, and third-party. These domains are increasingly interconnected, and managing them in isolation leads to blind spots, duplicated effort, and inconsistent reporting.
Platforms that support cross-domain integration provide a holistic view of risk exposure and empower better decisions, enabling organizations to:
-
Centralize risk data across functions
-
Harmonize control frameworks to avoid duplication across domains (e.g., mapping ISO 27001 controls to NIST CSF or SOC 2)
-
Correlate risks and incidents to understand root causes and cumulative impact
-
Standardize reporting and dashboards to provide a real-time, end-to-end view of organizational risk
3. Dynamic risk assessments
Traditional risk assessments—static, spreadsheet-based, and performed once or twice a year, are no longer sufficient. Modern threats evolve rapidly, and regulatory expectations demand more frequent and context-aware evaluations. Dynamic risk assessments adapt in real time, enabling continuous monitoring and faster response.
A dynamic approach allows organizations to:
-
Tailor assessments based on business unit, geography, or risk profile, adjusting risk questions accordingly
-
Integrate live data sources (e.g., vulnerability scans, threat intelligence feeds, cloud security posture tools) to enrich assessments with up-to-date evidence
-
Automate follow-ups and escalations when a control fails, a regulation changes, or a new asset is onboarded
-
Support multiple frameworks simultaneously, reducing duplication by reusing answers across ISO 27001, NIST CSF, SOC 2, and more
4. Third-party and supply chain risk management
Third-party and supply chain risks have become some of the most critical—and difficult to manage—threat vectors in modern risk programs. As organizations increasingly rely on external vendors, partners, and cloud providers to deliver core services, their risk surface expands far beyond traditional boundaries.
Modern risk programs must support:
-
Centralized vendor onboarding and due diligence
-
Risk-tiering and contextual assessments
-
Real-time monitoring of vendor security posture
-
Automated risk and issue detection from assessments
-
Consolidated reporting for boards and regulators
Choose a platform that can unify processes for onboarding, assessing, and monitoring vendors, classify vendors based on factors like data sensitivity and service criticality, and automate the generation of TPRM reports for audits and board oversight. AI tools can also help assess vendor documentation and identify control gaps or anomalies, improving coverage and reducing manual reviews.

5. Metrics for measuring success
Effective metrics go beyond volume-based reporting. They must reflect risk posture, control maturity, and business impact. For CISOs, risk officers, and compliance leads, robust metrics are essential for gaining executive support, prioritizing investment, and driving continuous improvement.
The most forward-thinking programs are moving toward real-time, risk-adjusted performance metrics such as:
|
Metric |
Why it matters |
|
Risk remediation time The average time it takes to address identified risks, particularly high-severity ones |
Reduces exposure windows and aligns risk management with business continuity |
|
Residual risk exposure The level of risk remaining after controls are applied |
Helps prioritize mitigation efforts and ensures that accepted risks remain within tolerance thresholds |
|
Control effectiveness rate The percentage of controls functioning as intended, validated through continuous control monitoring (CCM) |
Demonstrates whether your program is actually working in practice |
|
Assessment completion rate The number of assessments completed on time and how thorough or accurate they are |
Tracks the maturity and engagement of stakeholders in the risk process |
|
Incident-to-risk correlation rate The number of real-world incidents that align with previously identified risks |
Validates your risk assessment approach and feeds into root cause analysis |
|
Risk trends over time The evolution of risk exposure, categories, and response times over a period of time |
Identifies recurring issues, emerging risks, or slowdowns in response and informs leadership of systemic risks and long-term shifts in posture |
Modern platforms enhance these metrics with dynamic dashboards, data visualization tools, and drill-down analytics. With real-time, automated reports, teams can move from static reporting to decision-ready insights tailored to compliance teams, business units, or executive leadership.
The role of AI and automation in risk management
AI and automation aren’t just buzzwords; they’re critical to scaling risk management without adding headcount. Here's how advanced organizations are using them:
AI for proactive risk detection and response
Artificial intelligence is transforming how organizations detect, understand, and act on risks, freeing teams from manual reviews and improving consistency across assessments, audits, and frameworks.
Tools like 6clicks Hailey AI go far beyond simple keyword matching or automation scripts. They use natural language processing (NLP), machine learning, and semantic analysis to extract insights from unstructured data and identify risks that might otherwise go unnoticed.
With Hailey, organizations can:
-
Automatically flag risks from assessment responses, reducing the need for manual triage
-
Classify risks into relevant categories and link them to associated objects like controls, assets, and third parties
-
Identify control gaps by mapping existing controls to multiple requirements or frameworks in seconds
-
Generate risk treatment plans that align with contextual information and compliance requirements

This AI-driven process accelerates time to insight, reduces human error, and ensures that your risk register is always populated with accurate and actionable data.
Automation for continuous control monitoring
Continuous control monitoring (CCM) is quickly becoming a foundational element of modern risk and compliance programs. It moves organizations beyond point-in-time audits toward real-time assurance.
Modern platforms like 6clicks integrate with systems like Microsoft Defender, Wiz, or AWS to continuously monitor control performance and provide real-time visibility into:
-
Alignment with specific compliance requirements
-
Anomalies, configuration errors, and security issues
-
Control test results for automatic evidence collection
Traditionally, control testing was manual, periodic, and resource-intensive. But with automation, organizations can monitor control performance continuously, improving accuracy and agility.
Building scalable risk management operations
CISOs and risk leaders at growing organizations often face a key question: how do we scale risk management without scaling cost and complexity?
A modern approach includes:
Federated GRC
As organizations grow, managing risk and compliance centrally becomes limiting. Federated GRC offers a smarter approach—centralizing governance while allowing decentralized execution across business units, regions, or clients.
The 6clicks Hub & Spoke architecture brings this model to life:
-
The Hub governs policies, frameworks, and reporting
-
Spokes operate independently with localized risk and compliance activities
-
Templates, workflows, and content are shared from Hub to Spokes for consistency and speed
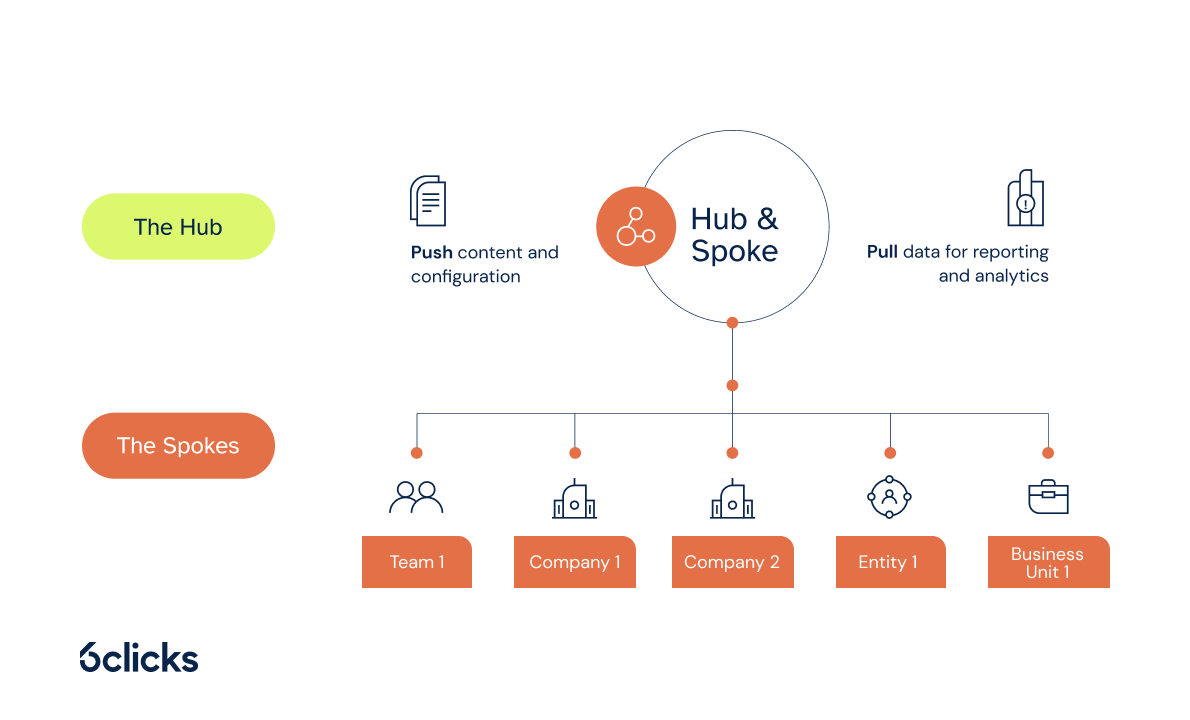
This architecture is ideal for enterprises and advisors seeking to scale GRC without losing control or flexibility.
Content-driven workflows
Pre-built risk libraries, policy and control sets, and assessment templates help accelerate implementation. Whether you're managing ISO 27001 certification, NIST CSF compliance, or aligning with regulatory frameworks, having built-in content mapped across frameworks significantly reduces time to value.
.png?width=1920&height=1080&name=Solution-get-ready-to-get-content-from-6clicks-library%20(1).png)
Out-of-the-box integrations
Modern risk management doesn’t operate in isolation—it relies on a connected ecosystem of tools spanning various functions across your business. Platforms like 6clicks offer out-of-the-box integrations that seamlessly connect with your existing tech stack so you can streamline data flow, enhance visibility, and automate workflows, enabling effective risk management at scale.
Key takeaways for CISOs and compliance leaders
Modern risk management is no longer just a compliance checkbox; it plays a central role in driving strategic outcomes. The most successful programs:
-
Align with business goals and adapt as risks evolve
-
Leverage AI and automation to reduce manual effort and improve accuracy
-
Break down silos between risk domains, enabling faster, smarter decisions
-
Prioritize scalability through architecture, content, and integrations
Whether you’re strengthening your enterprise risk management function or delivering GRC services to clients, adopting these principles will help you lead with confidence and resilience.
Get started with 6clicks
Ready to modernize your risk management program? Discover how 6clicks can help you unify, automate, and scale your approach with:
- An all-in-one platform for IT and enterprise risk management, vendor oversight, and incident management with a pre-built Content Library for turnkey deployment
-
Integrated control and compliance management with Continuous Control Monitoring for proactive risk mitigation and audit readiness
-
Next-generation AI capabilities for automating risk and issue identification, risk treatment, and control mapping and gap analysis
-
Built-in Reporting & Analytics with real-time dashboards and one-click report generation for instant access to insights such as high-priority risks, control test success rate, and more
-
Revolutionary Hub & Spoke architecture for centralized risk governance and localized execution



