6clicks Developer API
Integrate 6clicks with your cloud and business tools to extend and build custom GRC workflows.
Trusted by hundreds of CISOs, information security leaders and risk managers worldwide






.png?width=130&height=60&name=image%2048%20(2).png)

Unleash your cyber GRC program and drive collaboration
Workflow automation
Wider business engagment
Build on top of 6clicks
Securely build custom solutions to meet your exact operational and reporting requirements,
Leverage our comprehensive REST API to further automate your cyber GRC program
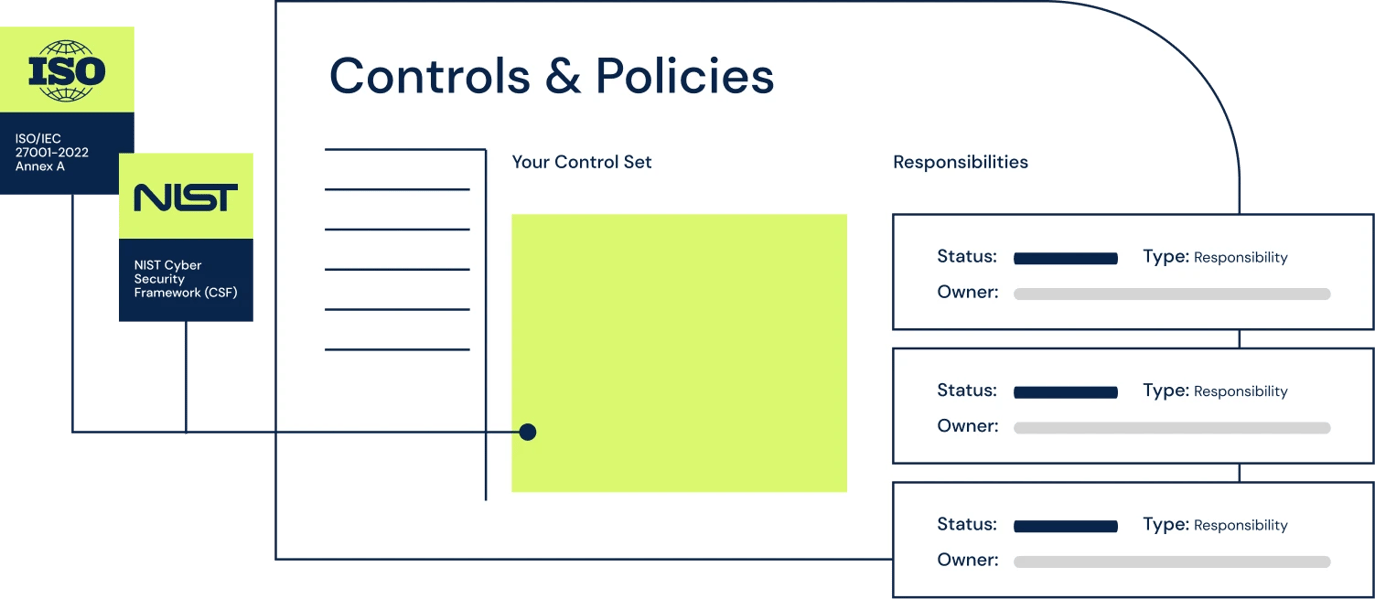
Manage all your controls in one place
Import, create and access hundreds of turn-key policies covering global cyber standards and regulations, and manage all your internal controls in one place. Assign owners and define recurring actionable tasks for manual and atuomated testing.
Create tests for automated control monitoring
Define automated tests and link them to controls. 6clicks' flexible testing framework allows you to create different tests depending on the data you want to pull from your cloud environments. Lastly, define the expected and failed test results and choose to set up automated notifications.
Simplified compliance management
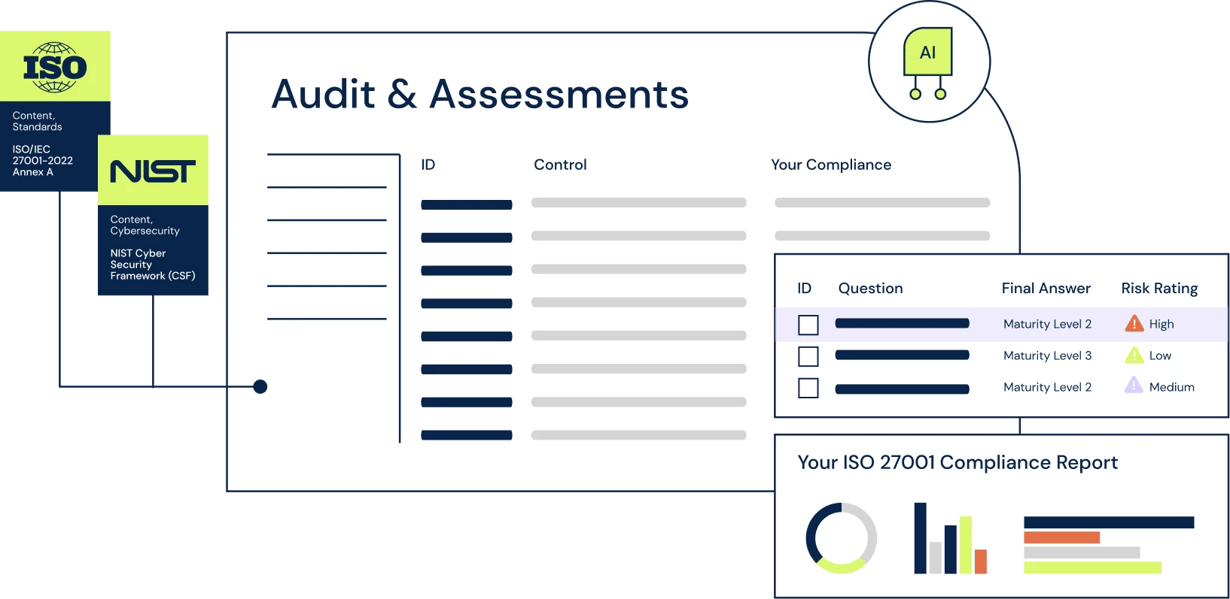
Leverage automated tests and related result collection for simplified and streamlined cyber compliance management by mapping controls and tests to various standards and regulations, such as NISFT CSF, ISO 27001, UK Cyber Essentials, DORA, and more. Streamline audits and assessments and get the true status of your cloud compliance through an up-to-date view of your security controls and combine with your manually tested controls to get the whole picture.

Autonomous evidence collection
Enhance your compliance process with automated evidence collection and near real-time remediation. Rapidly identify non-compliance issues and automate immediate, actionable alerts to control owners. Gain a comprehensive and transparent view of control effectiveness, ensuring swift compliance adherence and reducing manual effort in dynamic regulatory landscapes.
Dynamic dashboards and reporting
Achieve instant, insightful oversight of your cloud security with dynamic dashboards and detailed reports. Dive deep into near real-time control test statuses and issues, unlocking granular insights for informed decision-making.
Build custom GRC workflows
Integrate 6clicks with your technology ecosystem, build custom cyber GRC workflows, connect with cloud and business tools, and deeply embed your cyber GRC program into your organization.
Trigger internal and external events
Trigger internal tasks like creating risks and issues based on external events, and initiate external workflows from 6clicks events, such as status changes or assessment completions.
Export and integrate data for advanced reporting
Programmatically pull data from 6clicks into custom reports, documents, and BI tools like PowerBI and Tableau, combining with other data sources for complete reporting flexibility.
Build custom control test
Extend 6clicks’ continuous control monitoring capability and run test against systems that 6clicks does not integrate with, such as on-prem or custom applications.
Related articles
Keep up to date with what's new and our thought leadership.

6clicks renews UK Cyber Essentials Plus certification, reinforcing trusted GRC platform for government and defence
London, United Kingdom – 27 February 2026. 6clicks, a global leader in AI-powered governance, risk, and compliance (GRC) software, has successfully...

Navigating Middle East cybersecurity compliance: A guide for GCC organisations
The Gulf Cooperation Council (GCC) region has undergone a dramatic transformation in its approach to cybersecurity and data sovereignty. At the heart...

Achieving sovereign regulatory assurance in today’s threat and AI-driven world
Cyber threats are escalating. AI systems are becoming more prevalent in regulated environments. Digital networks and critical infrastructure are...

6clicks brings cyber and GRC leaders together to advance sovereign AI assurance in the GCC
Dubai, United Arab Emirates – 16 January 2026. 6clicks, a leading AI-powered governance, risk, and compliance (GRC) platform, hosts “The 2026...
Intelligently accelerate your cyber risk and compliance program today




